Table of Contents
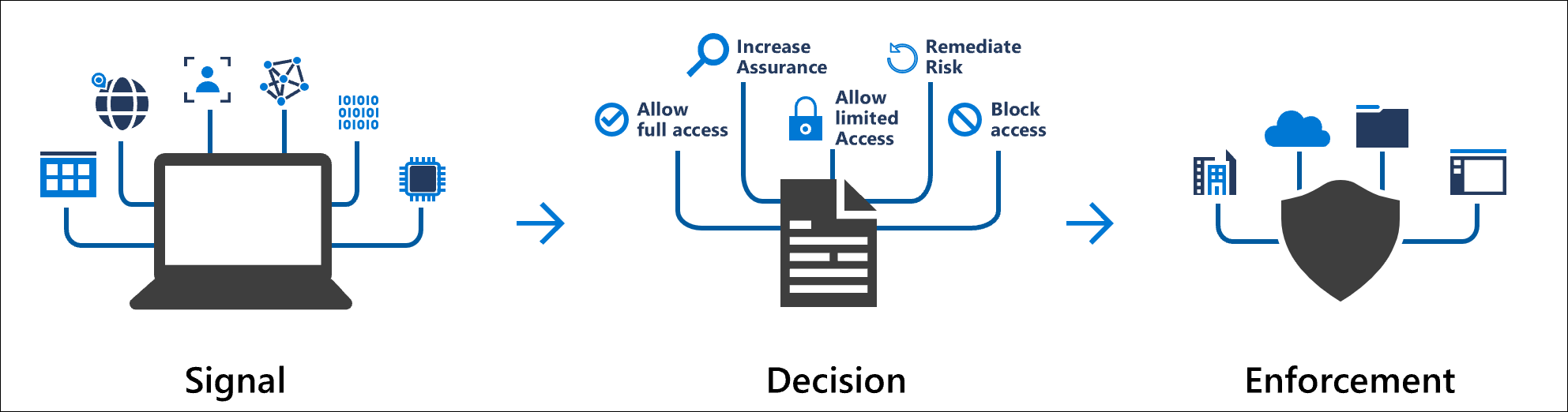
Modern security demands extend beyond the traditional network perimeter, encompassing user and device identities. Organizations increasingly rely on identity-driven signals to make access control decisions. Microsoft Entra Conditional Access integrates these signals into a unified policy engine to enforce security measures and organizational policies effectively. Acting as Microsoft’s Zero Trust policy engine, Conditional Access evaluates signals from various sources to implement policies dynamically.
How Conditional Access Policies Work
At their core, Conditional Access policies function as if-then statements. For example:
- If a user wants to access Microsoft 365,
- Then they must perform multi-factor authentication (MFA).
These policies strike a balance between two primary objectives:
- Empowering users to remain productive anywhere, anytime.
- Safeguarding organizational assets with robust access controls.
Note: Conditional Access policies activate after the initial authentication is complete. While they aren’t designed to prevent denial-of-service (DoS) attacks, they can leverage signals from such events to guide access decisions.
Common Signals Used in Conditional Access
Conditional Access leverages various signals to determine access:
- User or Group Membership
- Policies can target specific users or groups for fine-grained control.
- IP Location Information
- Trusted IP ranges can be defined for policy decisions.
- Organizations can block or allow traffic from specific countries or regions.
- Device State and Filters
- Policies can apply to devices based on their platform or compliance state.
- Filters enable targeting of specific devices, such as privileged access workstations.
- Application Access
- Policies can be triggered when users attempt to access specific applications.
- Risk Detection
- Integration with Microsoft Entra ID Protection helps detect and mitigate risky sign-ins and user behavior in real time.
- Microsoft Defender for Cloud Apps
- Enhances visibility and control by monitoring and managing user activities in cloud environments.
Common Access Decisions
Conditional Access policies can enforce two primary decisions:
- Block Access
- The most restrictive option, completely denying access.
- Grant Access
- Allows access under conditions, such as:
- Requiring MFA or authentication strength.
- Ensuring the device is compliant.
- Mandating the use of approved client apps.
- Enforcing app protection policies or password changes.
- Allows access under conditions, such as:
Commonly Applied Policies
Organizations frequently use Conditional Access policies to address specific concerns, such as:
- Enforcing MFA for administrative roles or Azure management tasks.
- Blocking sign-ins using legacy authentication protocols.
- Requiring trusted locations for security information registration.
- Restricting access to organization-managed devices for specific applications.
- Blocking risky sign-in attempts or access from certain locations.
Policies can be created from scratch, through templates, or using the Microsoft Graph API.
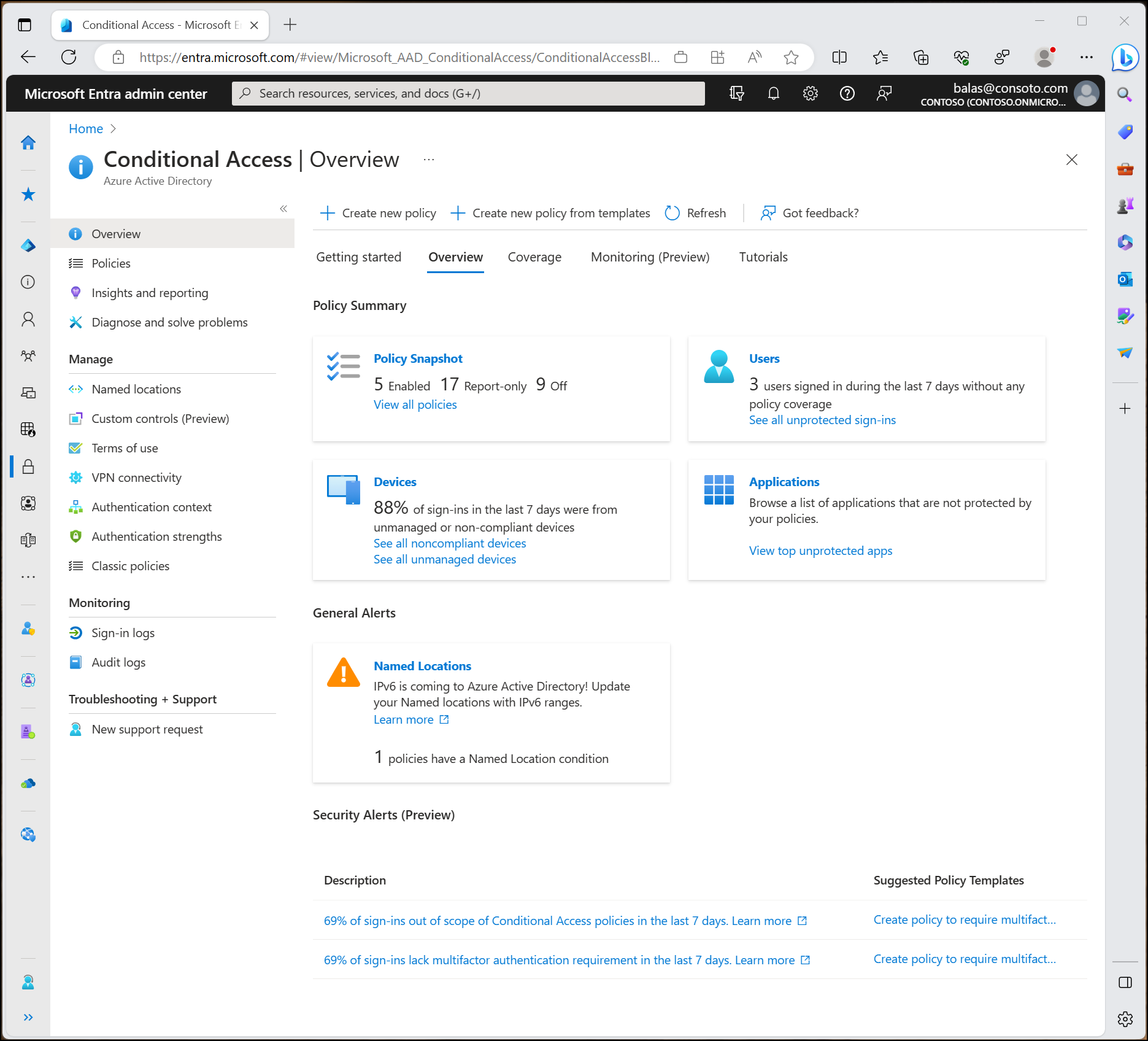
Admin Experience with Conditional Access
Administrators with the Conditional Access Administrator role can manage policies via the Microsoft Entra Admin Center under Protection > Conditional Access. Key features include:
- Overview Page:
- Provides summaries of policy states, users, devices, applications, and alerts.
- Coverage Page:
- Offers insights into application coverage by Conditional Access policies.
- Monitoring Page:
- Displays graphs of sign-ins with filtering options to identify policy gaps.
- Policies Page:
- Enables filtering policies by actor, target resource, conditions, controls applied, state, or date for quick navigation.
License Requirements
- Basic Conditional Access: Requires a Microsoft Entra ID P1 license.
- Risk-Based Policies: Require Microsoft Entra ID P2 licenses.
- Microsoft 365 Business Premium: Provides access to Conditional Access features.
Licenses for interacting products and features, like Microsoft Defender for Cloud Apps, must also be acquired. If licenses expire, policies remain active but cannot be updated.
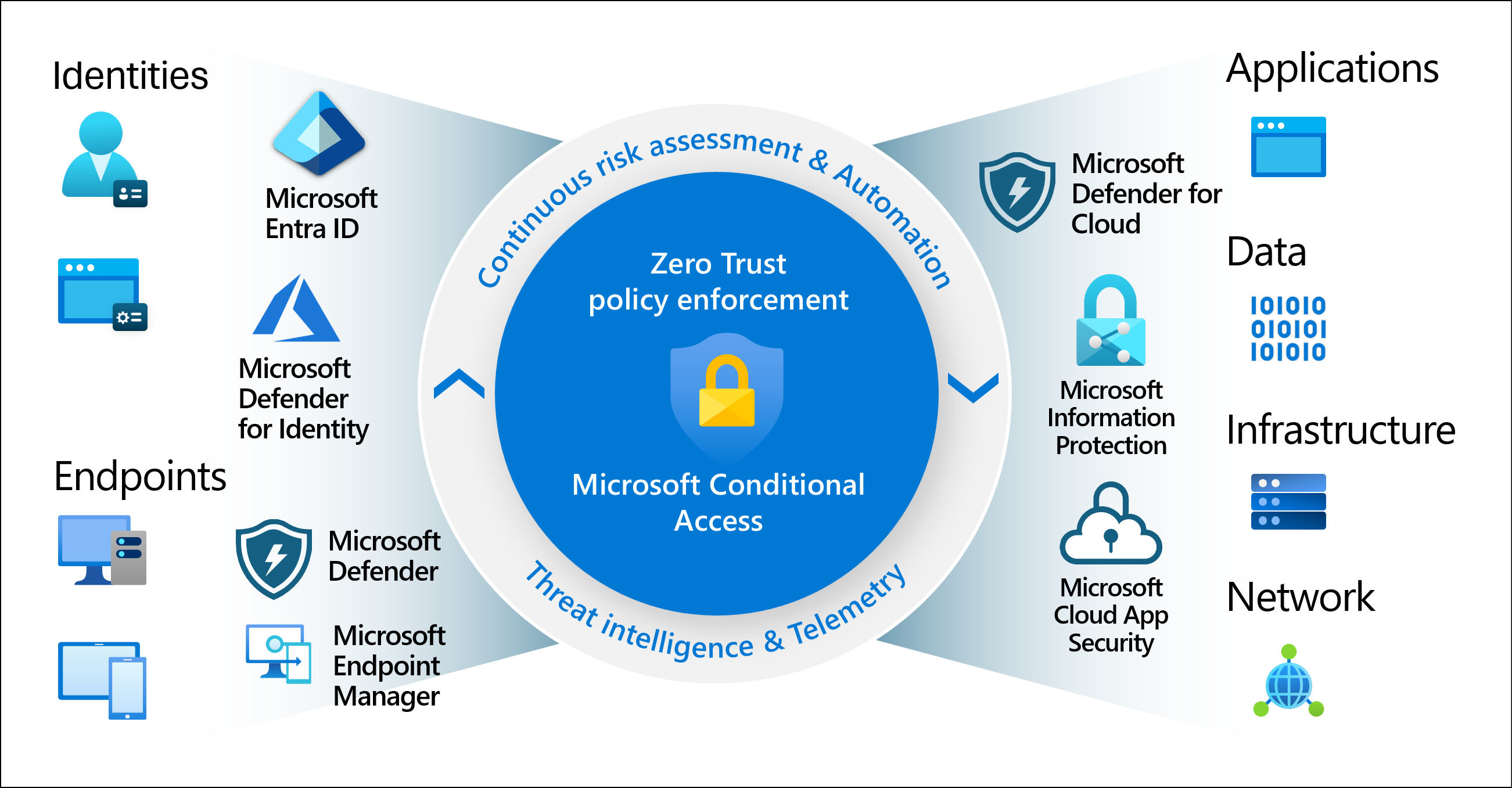
Zero Trust Principles
Microsoft Entra Conditional Access aligns with the core principles of a Zero Trust architecture:
- Verify Explicitly: Always authenticate and authorize based on all available data points.
- Use Least Privilege Access: Grant the minimal access necessary.
- Assume Breach: Treat every access request as though it originates from an open network.
For more guidance on Zero Trust strategies, visit the Zero Trust Guidance Center.
Microsoft Entra Conditional Access simplifies managing security policies while ensuring productivity and robust protection. By leveraging its capabilities, organizations can adopt modern security practices aligned with Zero Trust principles.
For more insights and updates, follow Cerebrix on social media at @cerebrixorg.
💡 You might also like:
Franck Kengne
Tech Visionary and Industry Storyteller
Read also
January 15, 2025
January 14, 2025
January 14, 2025