Table of Contents
In today’s cloud-driven world, security is more critical than ever, especially when it comes to managing and deploying code through DevOps pipelines. For Atlassian, a leading provider of collaboration tools like JIRA, Confluence, and Bitbucket, security is paramount. As a company that relies heavily on cloud infrastructure and delivers products to millions of users globally, ensuring the integrity and security of their development pipeline is essential.
In this case study, we’ll examine how Atlassian leveraged cloud-native security tools to secure its DevOps pipelines, address vulnerabilities, and maintain the balance between speed and security. We’ll explore their challenges, the cloud-native tools they implemented, and the resulting transformation in their security posture.
Challenges Faced by Atlassian
As a company that supports agile development practices across diverse teams, Atlassian needed to secure its DevOps pipelines without slowing down its rapid development cycles. Some of the key challenges they faced included:
- Inconsistent Security Policies: Security measures were not uniformly applied across different stages of the pipeline, creating potential gaps and vulnerabilities.
- Open-Source Dependencies: The reliance on open-source libraries introduced the risk of vulnerabilities in third-party code.
- Manual Security Processes: Some security checks were performed manually, leading to bottlenecks and inconsistencies across teams.
- Balancing Speed with Security: With a strong emphasis on continuous integration and deployment, Atlassian needed to ensure that security processes didn’t hinder the speed of releases.
Given these challenges, Atlassian decided to integrate cloud-native security tools into its pipeline to automate security and achieve consistency across their development lifecycle.
Solution: Cloud-Native Security Tools Integration
To address these challenges, Atlassian deployed a combination of cloud-native security tools that integrated seamlessly with their existing DevOps practices. Here’s a breakdown of the tools they implemented:
1. AWS Security Hub for Centralized Security Management
Since Atlassian runs a significant portion of its infrastructure on AWS, the company leveraged AWS Security Hub to centralize its security operations. Security Hub aggregates security findings from various AWS services such as Amazon GuardDuty, Amazon Inspector, and AWS Config, allowing Atlassian to monitor security risks across its AWS resources in real time.
- Benefit: Centralized visibility over the security of all AWS accounts and services.
- Outcome: Improved incident response times and more efficient monitoring of security alerts.
2. Infrastructure as Code (IaC) Security with Checkov
Atlassian uses Terraform and Pulumi for provisioning cloud infrastructure. To secure their Infrastructure as Code (IaC), Atlassian integrated Checkov, a tool that scans Terraform and Pulumi configurations for misconfigurations before deployment.
- Benefit: Early detection of potential security risks in infrastructure configurations, such as misconfigured access controls or overly permissive IAM roles.
- Outcome: Proactive prevention of misconfigurations reaching production environments, reducing security risks in cloud infrastructure.
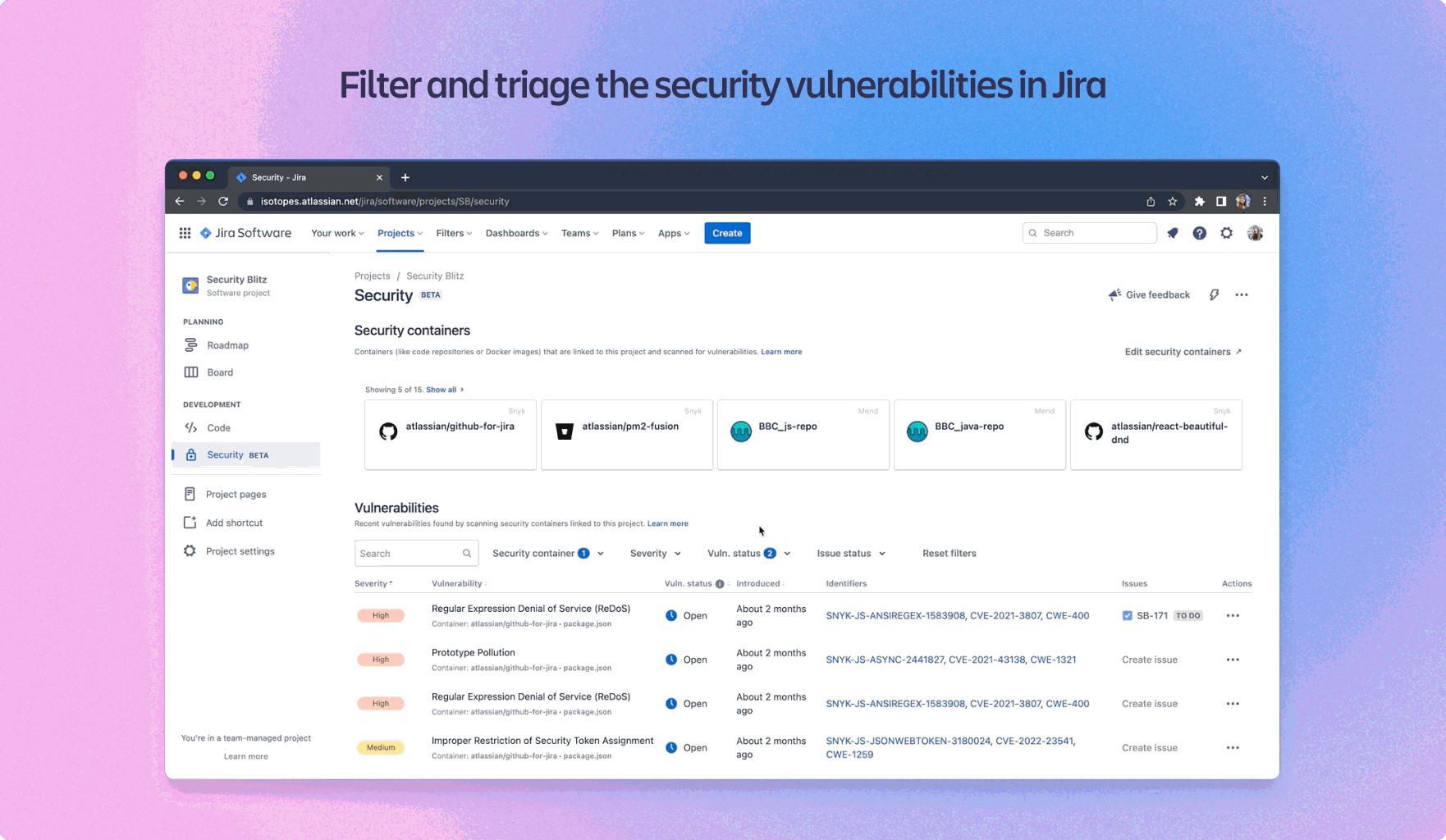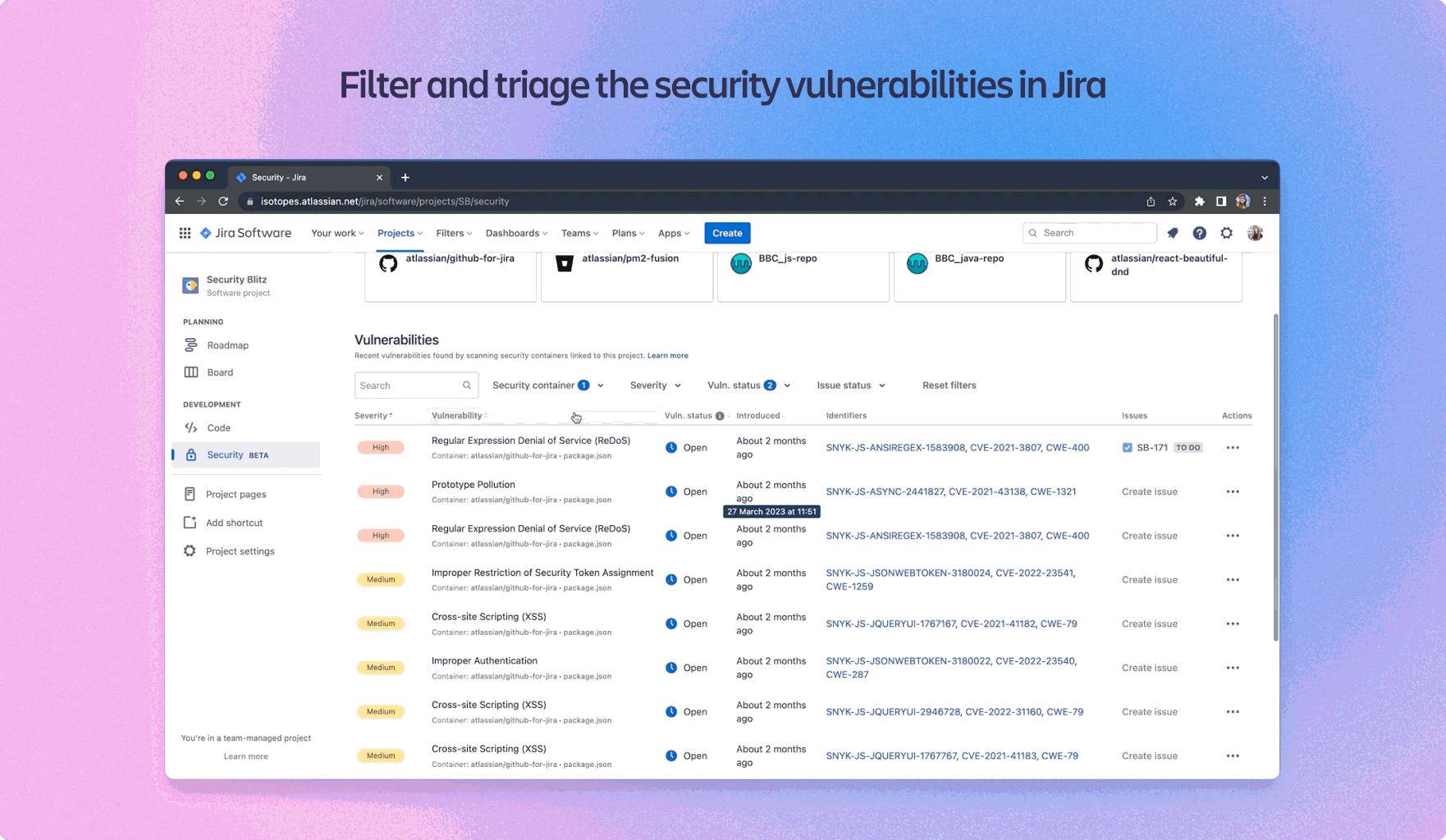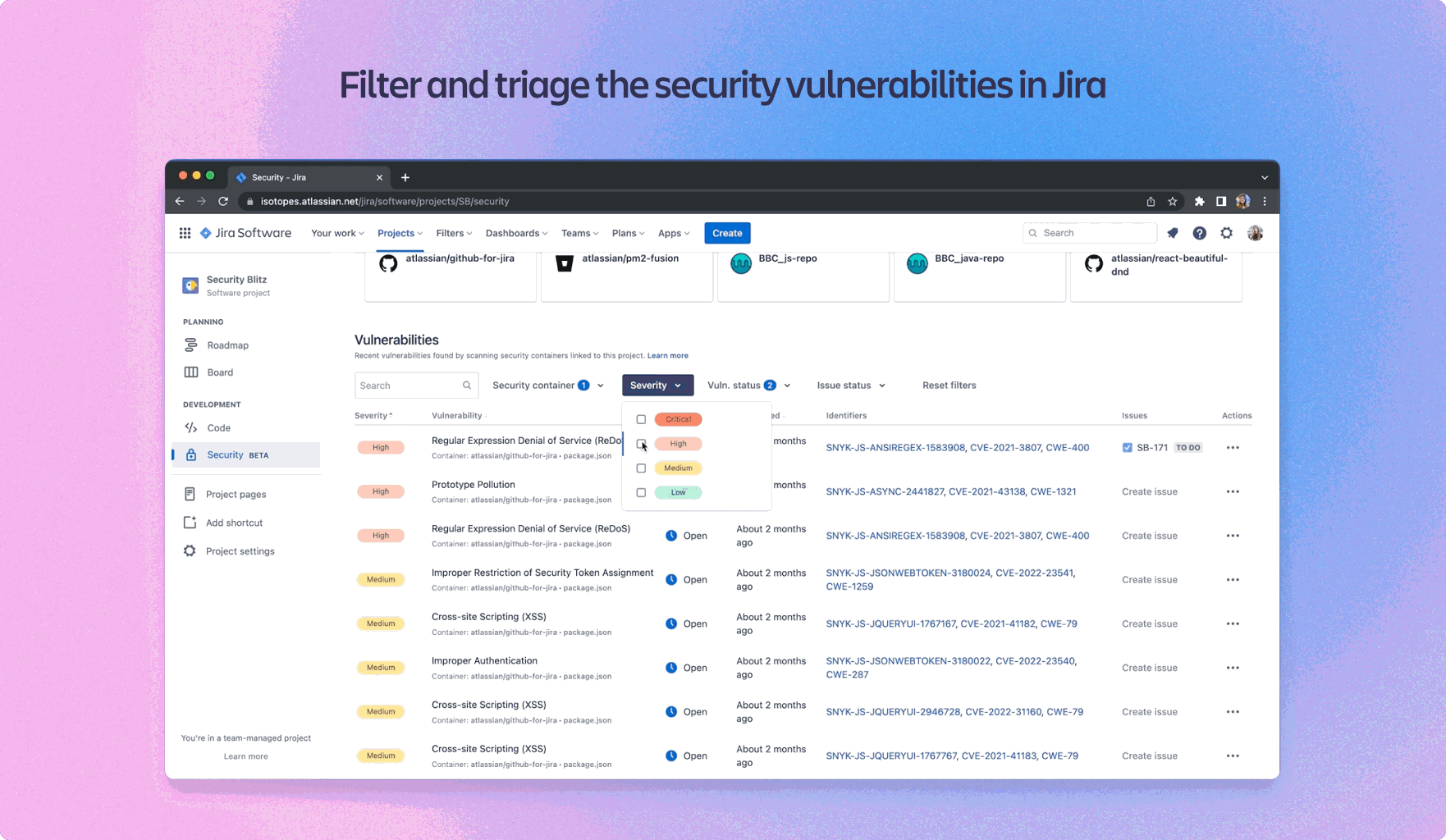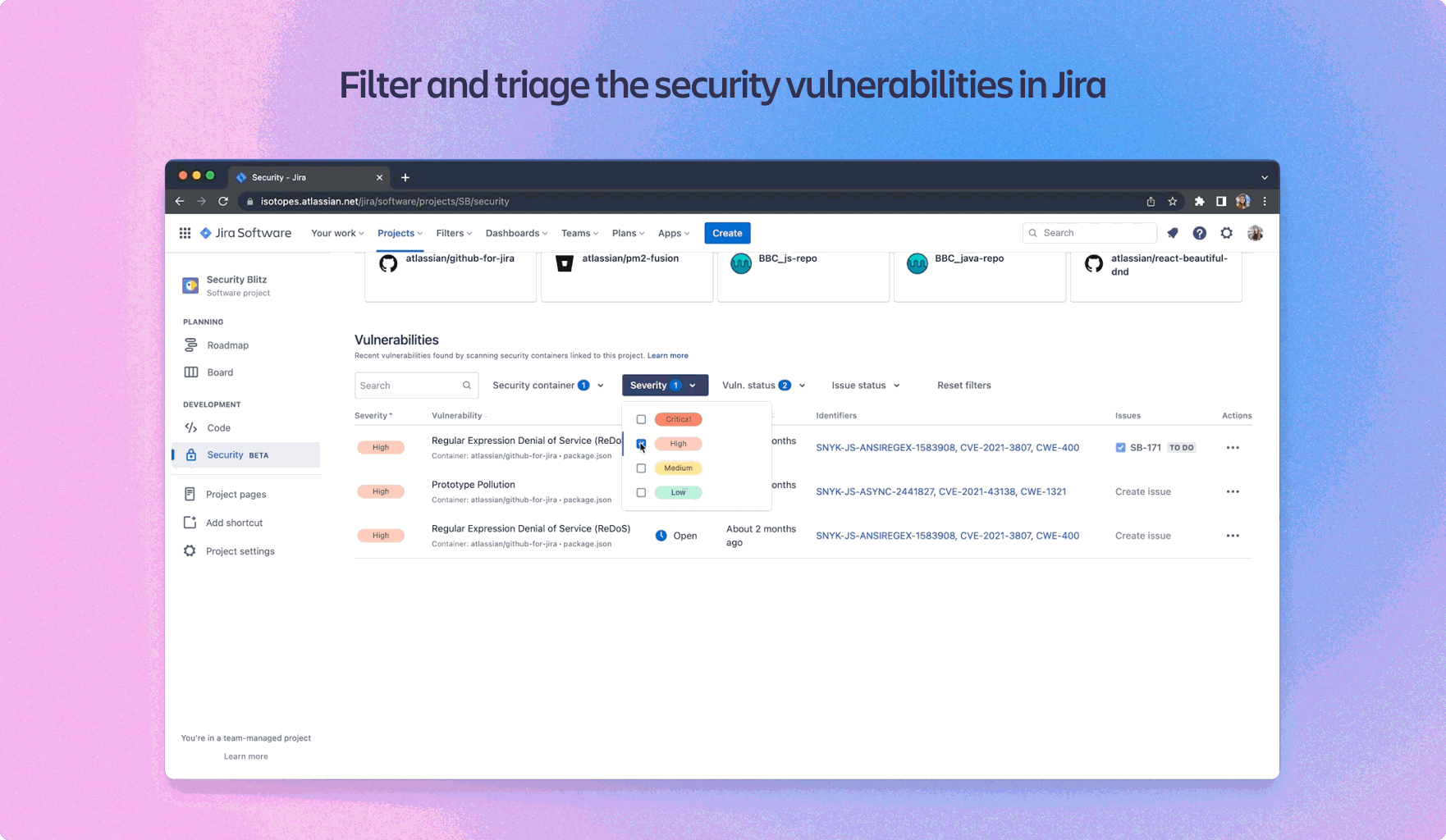
3. Snyk for Open-Source Dependency Scanning
Atlassian relies heavily on open-source libraries, and managing vulnerabilities in these dependencies is critical. By integrating Snyk into their CI/CD pipeline, Atlassian automated the scanning of dependencies for known vulnerabilities.
- Benefit: Automated vulnerability scanning of third-party dependencies, with real-time alerts and remediation recommendations.
- Outcome: Atlassian reduced the risk of vulnerable libraries being deployed, improving the overall security of their software.
4. Container Security with Aqua Security
As Atlassian adopted containerization for deploying their applications, securing containers became a priority. They integrated Aqua Security to scan container images before deployment and monitor containers during runtime.
- Benefit: Comprehensive container security, including vulnerability scanning, runtime monitoring, and enforcement of security policies.
- Outcome: Atlassian was able to ensure that only secure containers were deployed, while monitoring for any suspicious activity in production.
5. Kubernetes Security with Kube-bench and Kube-hunter
For Kubernetes-based workloads, Atlassian deployed Kube-bench and Kube-hunter to evaluate and strengthen the security of their Kubernetes clusters.
- Benefit: Regular Kubernetes cluster security assessments to ensure compliance with the CIS Kubernetes Benchmark and identify potential weaknesses.
- Outcome: Improved cluster security and better visibility into Kubernetes-specific vulnerabilities, reducing the attack surface.
Key Results of Cloud-Native Security Implementation
By integrating cloud-native security tools into their DevOps pipeline, Atlassian was able to achieve several key outcomes:
- Shift-Left Security: Security became embedded earlier in the development lifecycle, allowing developers to address vulnerabilities and misconfigurations before they reached production. Tools like Snyk and Checkov provided automated feedback directly to developers, helping them catch issues earlier and fix them faster.
- Increased Automation and Efficiency: Manual security checks were replaced with automated security scans, reducing bottlenecks in the DevOps process. The use of AWS Security Hub provided a centralized platform to manage security findings and automate responses to common security issues.
- Improved Incident Response: With tools like GuardDuty and Aqua Security monitoring production environments in real-time, Atlassian’s security team was able to respond to threats more quickly, reducing the risk of security incidents affecting customers.
- Compliance with Best Practices: By integrating Kube-bench and Checkov, Atlassian ensured compliance with industry security benchmarks such as the CIS Kubernetes Benchmark and other cloud security standards. This helped maintain high security standards and provided peace of mind in audit and compliance scenarios.
- Continuous Monitoring and Remediation: Continuous scanning of both infrastructure and applications (via Snyk and Aqua Security) ensured that vulnerabilities, misconfigurations, and threats were detected and addressed throughout the DevOps cycle, reducing the time to remediation.
Use Case Example: Securing Bitbucket Pipelines
Atlassian’s use of Bitbucket Pipelines for continuous integration and delivery provided an ideal integration point for cloud-native security tools. Here’s how they secured their pipeline:
- Source Code Scanning: When developers commit code to Bitbucket, Snyk automatically scans the codebase for known vulnerabilities in open-source libraries and provides suggestions for remediation.
- Infrastructure Security: Before deploying infrastructure changes via Terraform, Checkov scans the configuration files for security misconfigurations, ensuring that only secure infrastructure is deployed.
- Container Security: Once the build process generates Docker containers, Aqua Security scans the container images for vulnerabilities and ensures they meet security policies before deployment.
- Runtime Security: Post-deployment, Aqua Security monitors running containers for any anomalous behavior, and AWS Security Hub aggregates security findings across AWS accounts, ensuring real-time alerts for any suspicious activities.
This workflow allowed Atlassian to seamlessly integrate security into their Bitbucket Pipelines without slowing down their development cycles.
Conclusion: Lessons from Atlassian’s Cloud-Native Security Transformation
Atlassian’s successful integration of cloud-native security tools into their DevOps pipeline provides a valuable lesson for other organizations looking to improve their security posture while maintaining speed and agility. The key takeaways from Atlassian’s approach include:
- Automate security as early as possible: By shifting security left and embedding it directly into the development process, Atlassian significantly reduced vulnerabilities before they reached production.
- Use cloud-native tools for real-time monitoring: Cloud-native tools like AWS Security Hub and Aqua Security provided centralized monitoring and response capabilities, allowing Atlassian to maintain control over their entire cloud infrastructure.
- Leverage continuous security assessments: Tools like Snyk, Checkov, and Kube-bench enabled continuous scanning and assessment of the codebase, infrastructure, and Kubernetes clusters, ensuring that vulnerabilities and misconfigurations were detected and remediated before they could be exploited.
By embracing a cloud-native security approach, Atlassian was able to fortify its DevOps pipeline, ensuring secure, scalable, and efficient development practices that align with modern business needs.
For more case studies on cloud security and DevOps, follow @cerebrixorg on social media!
Franck Kengne
Tech Visionary and Industry Storyteller
Read also
November 19, 2024
November 19, 2024
November 19, 2024